We only use cookies that are strictly necessary for our website and services to work.
Defend your mailboxes with PhishTool Enterprise. Find out more
Stop trying to avoid phishing. Choose a weapon and fight it...
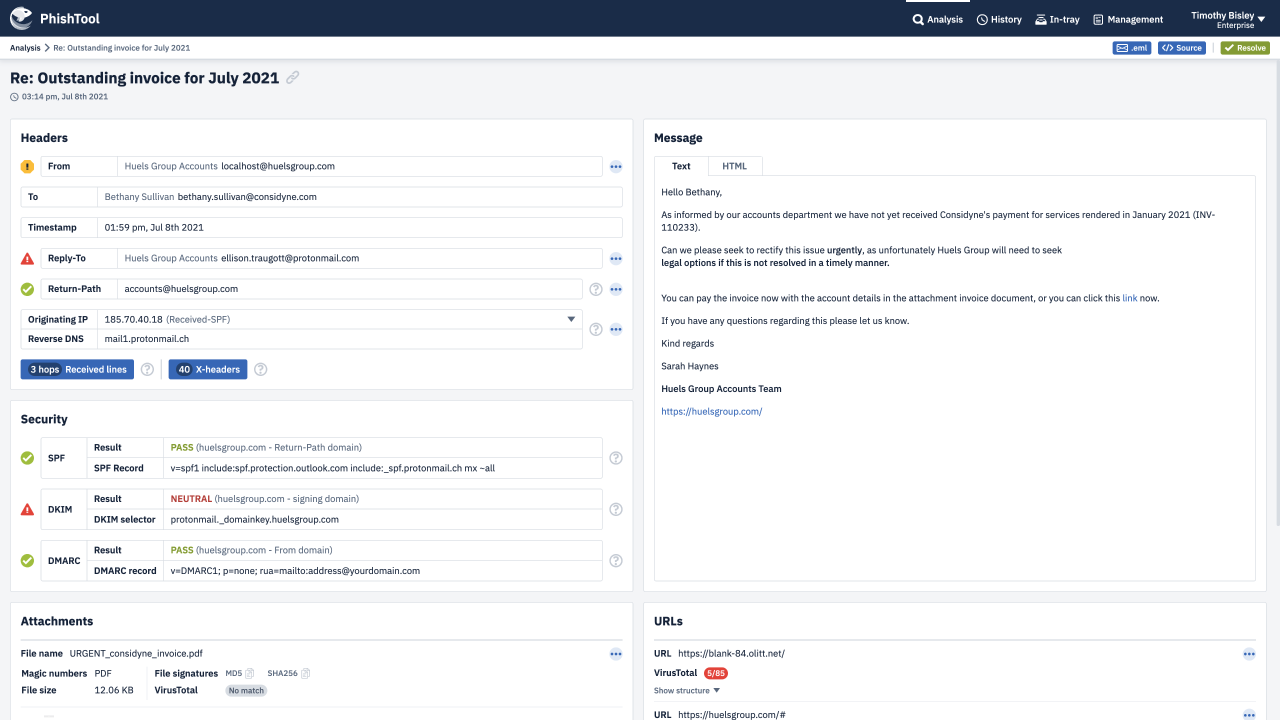
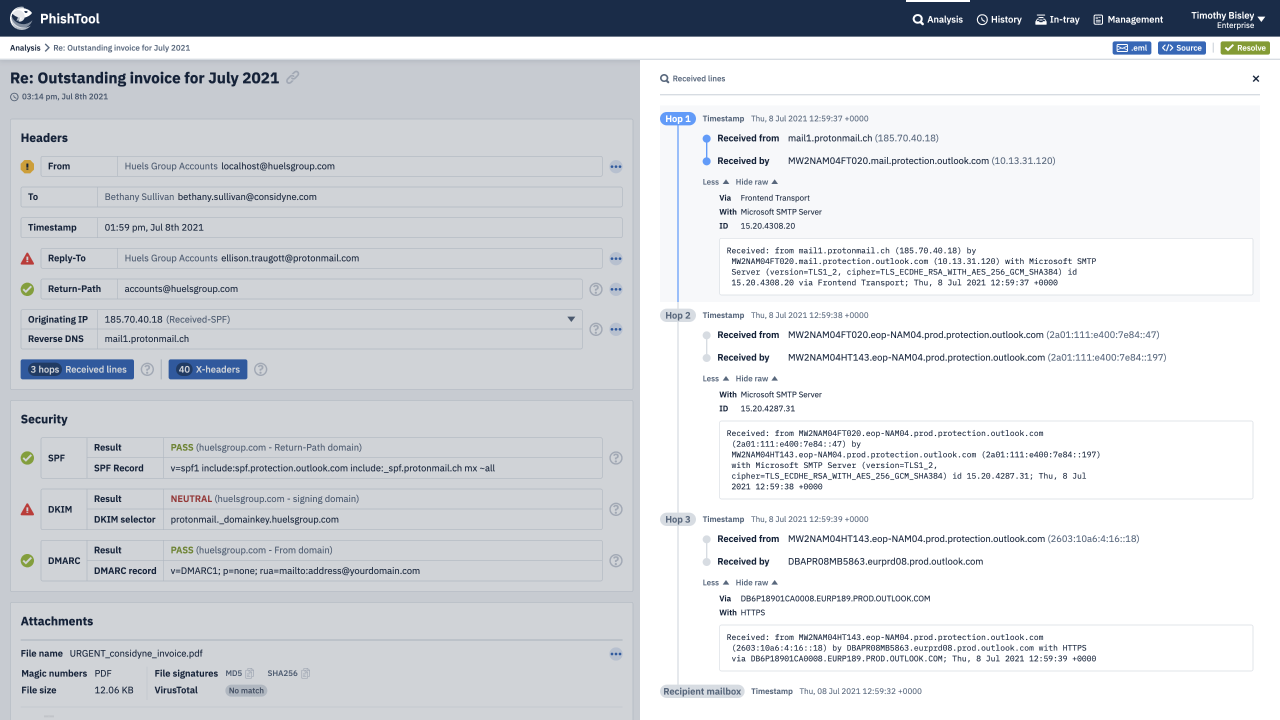
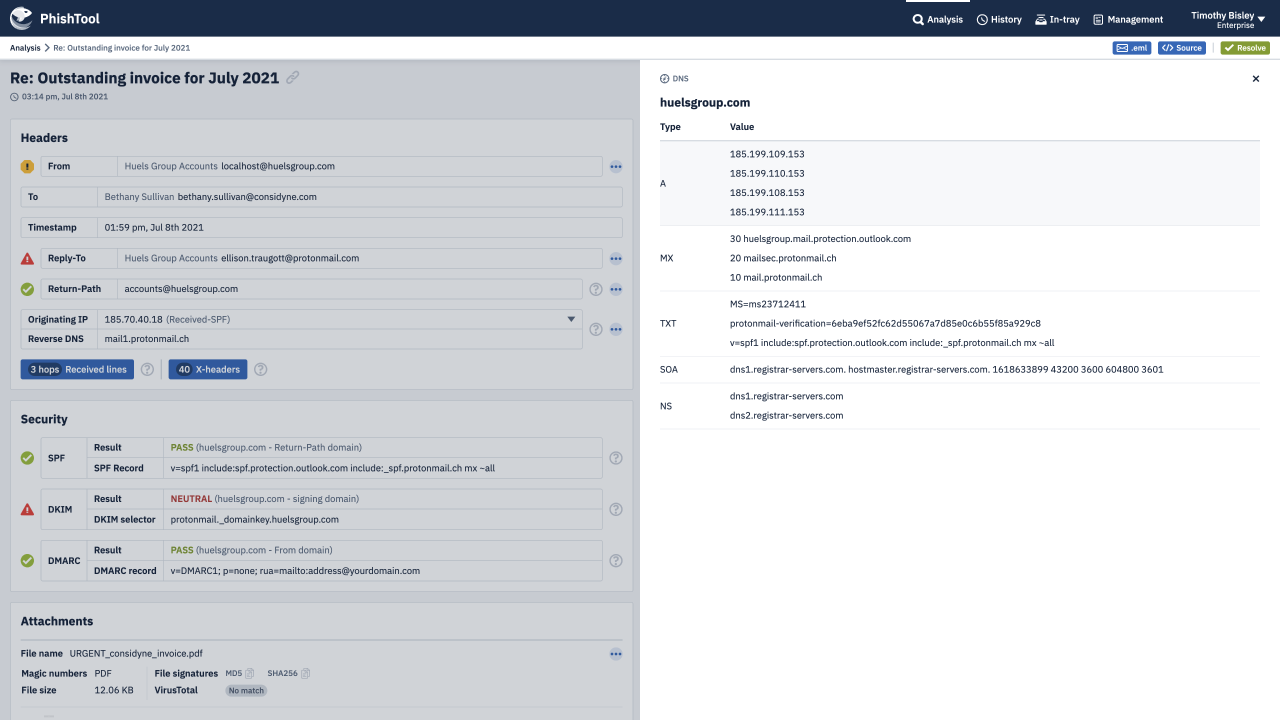
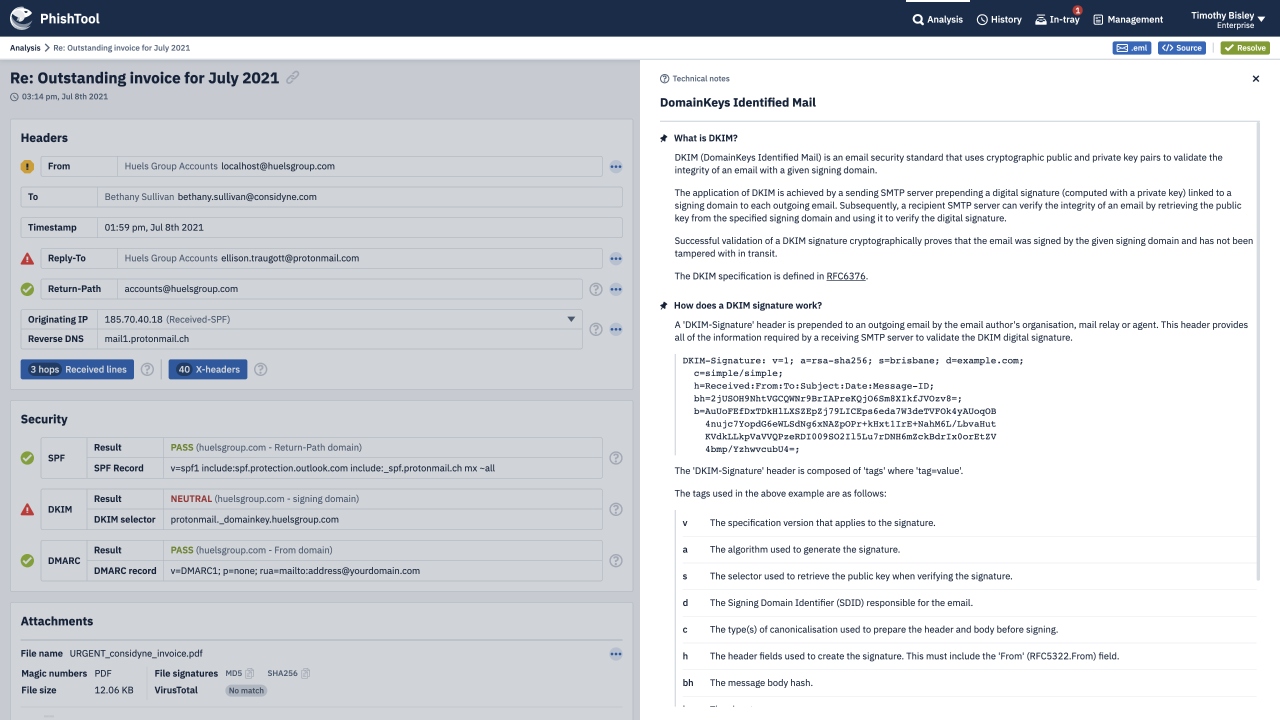
PhishTool gives human analysts the power to reverse engineer phishing emails, to better defend against them. PhishTool is to phishing emails as a disassembler is to malware or a forensic toolkit is to file systems.
Formidable in the face of phishing
Be you a security researcher investigating a new phish-kit, a SOC analyst responding to user reported phishing, a threat intelligence analyst collecting phishing IoCs or an investigator dealing with email-born fraud.
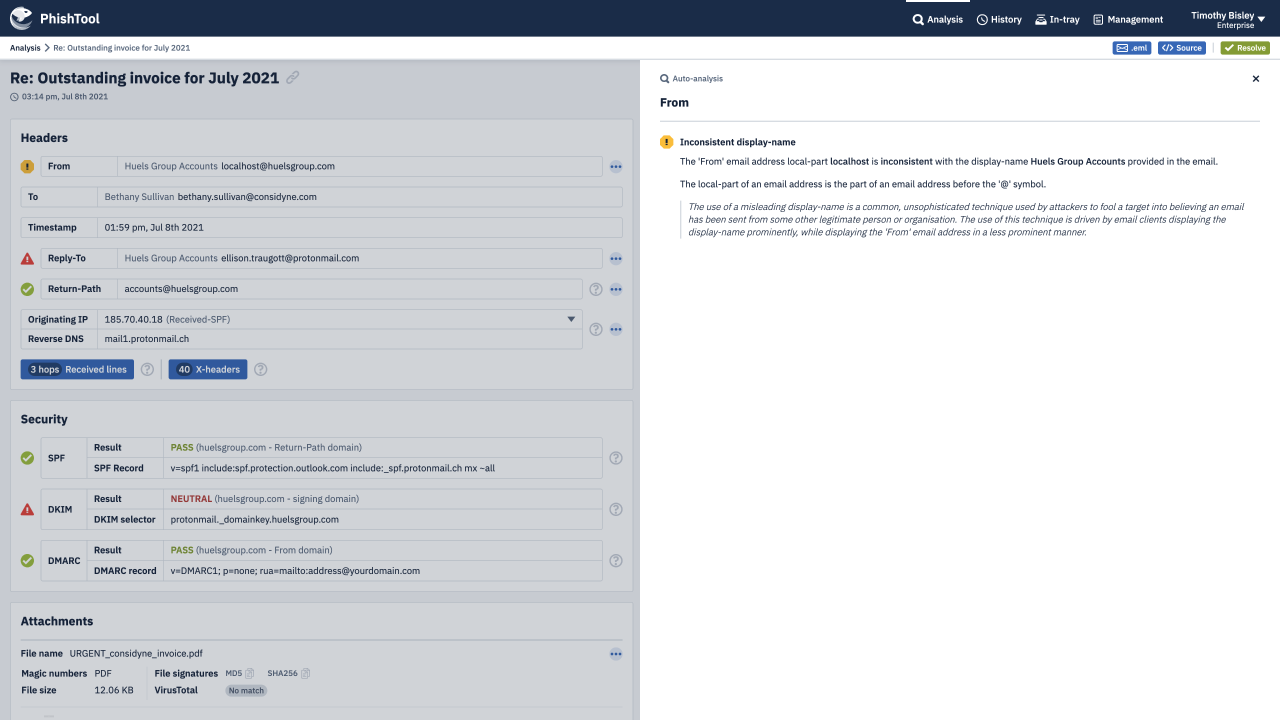
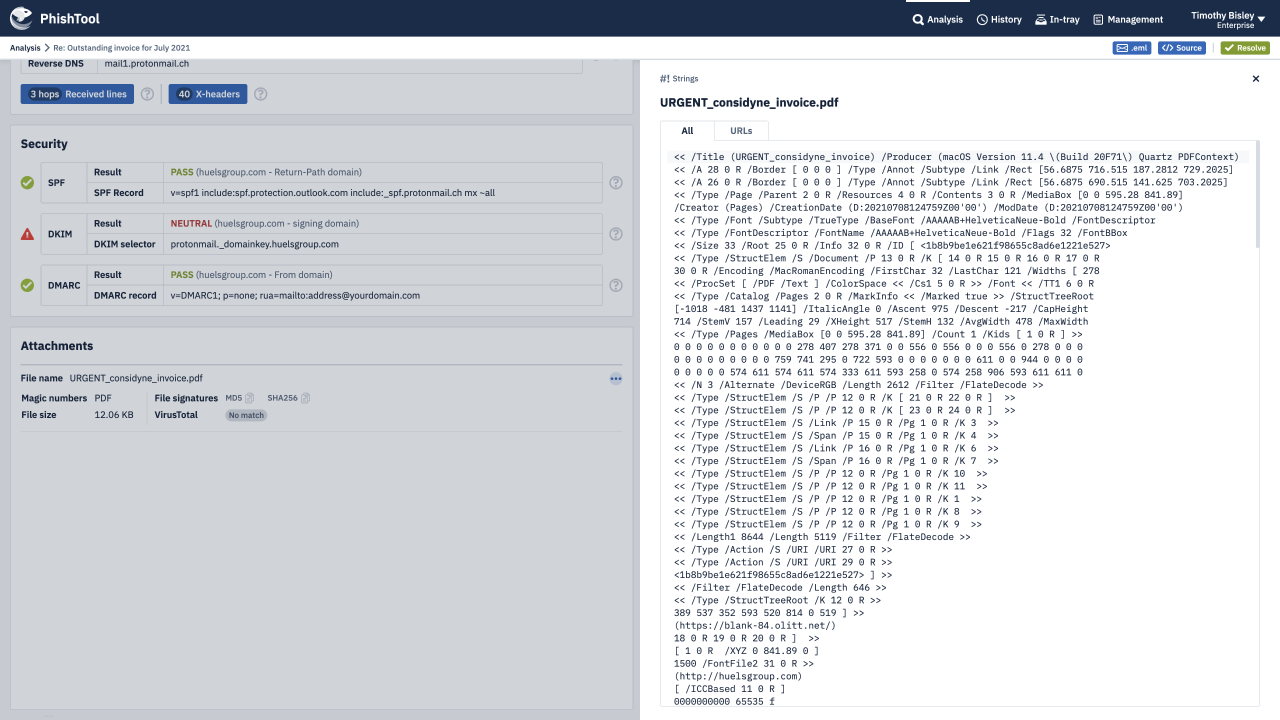
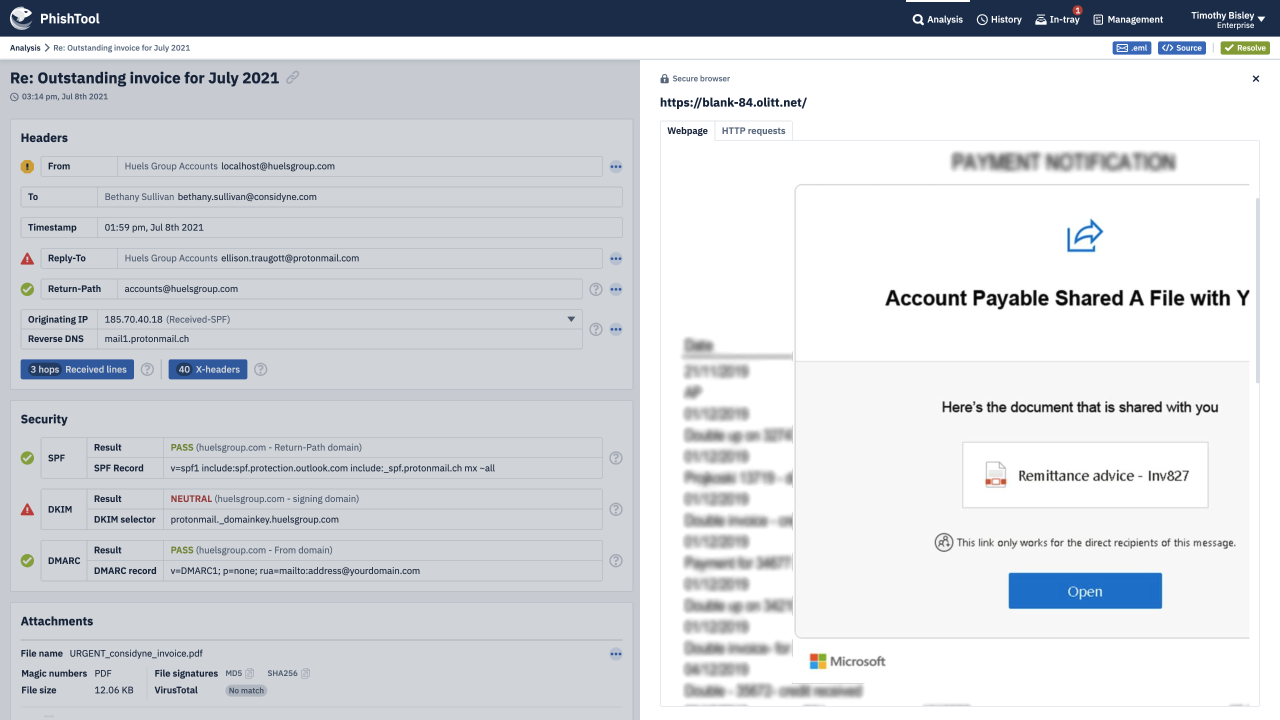
PhishTool combines threat intelligence, OSINT, email metadata and battle tested auto-analysis pathways into one powerful phishing response platform. Making you and your organisation a formidable adversary - immune to phishing campaigns that those with lesser email security capabilities fall victim to.
Try PhishTool Community nowPowerful and intuitive phishing response
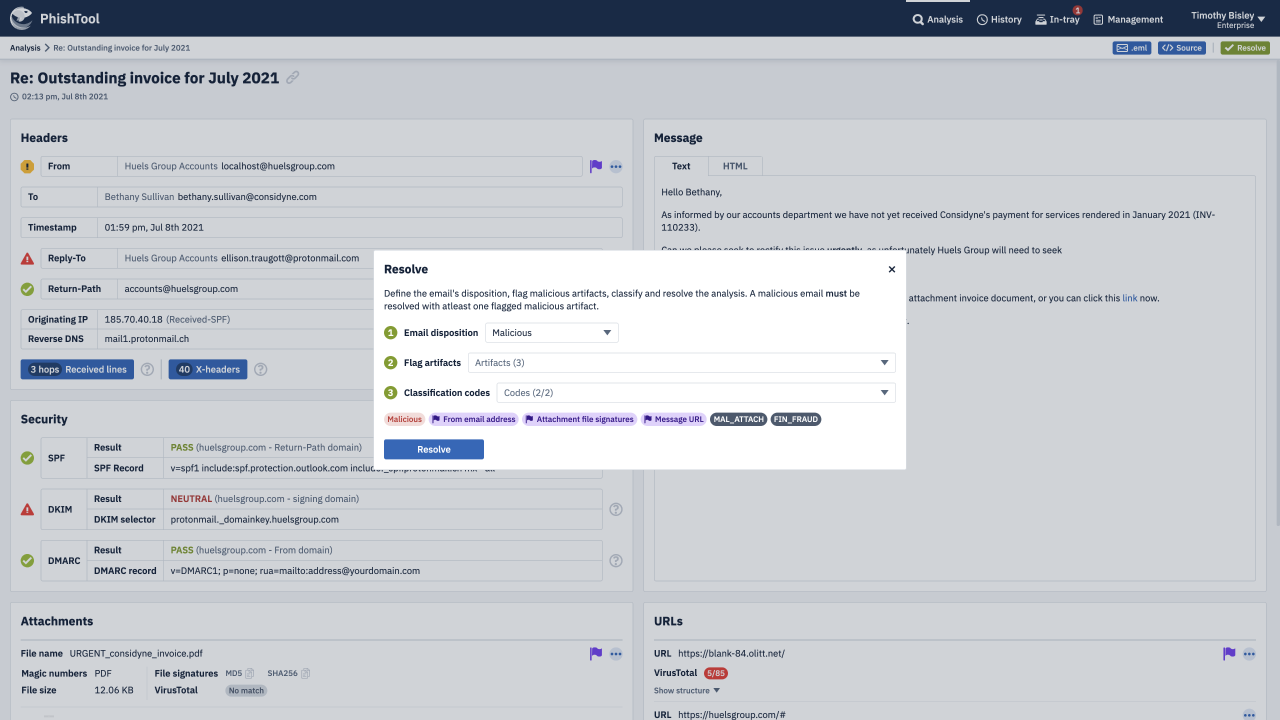
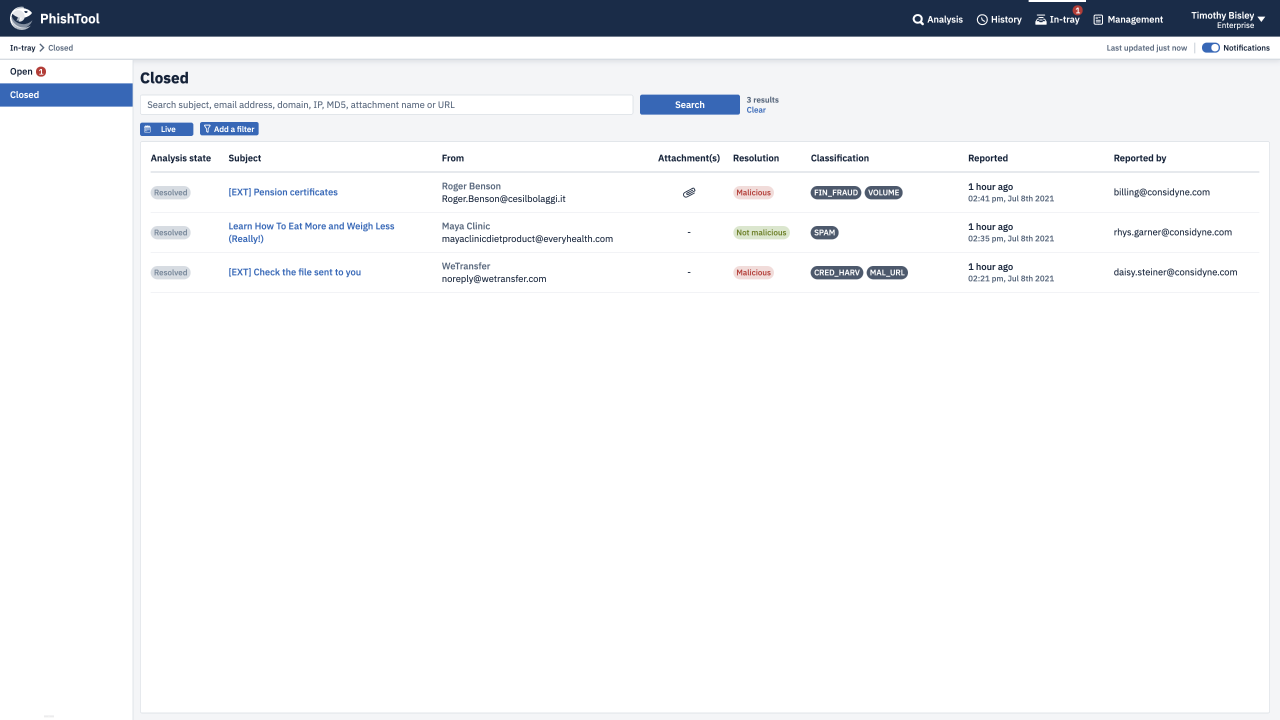
Through an intuitive UI, guided auto-analysis pathways, powerful contextual analysis of email metadata and embedded email expertise, PhishTool provides you with actionable findings from phishing emails, protecting you, your organisation and the world from the latest, most devastating phishing campaigns.
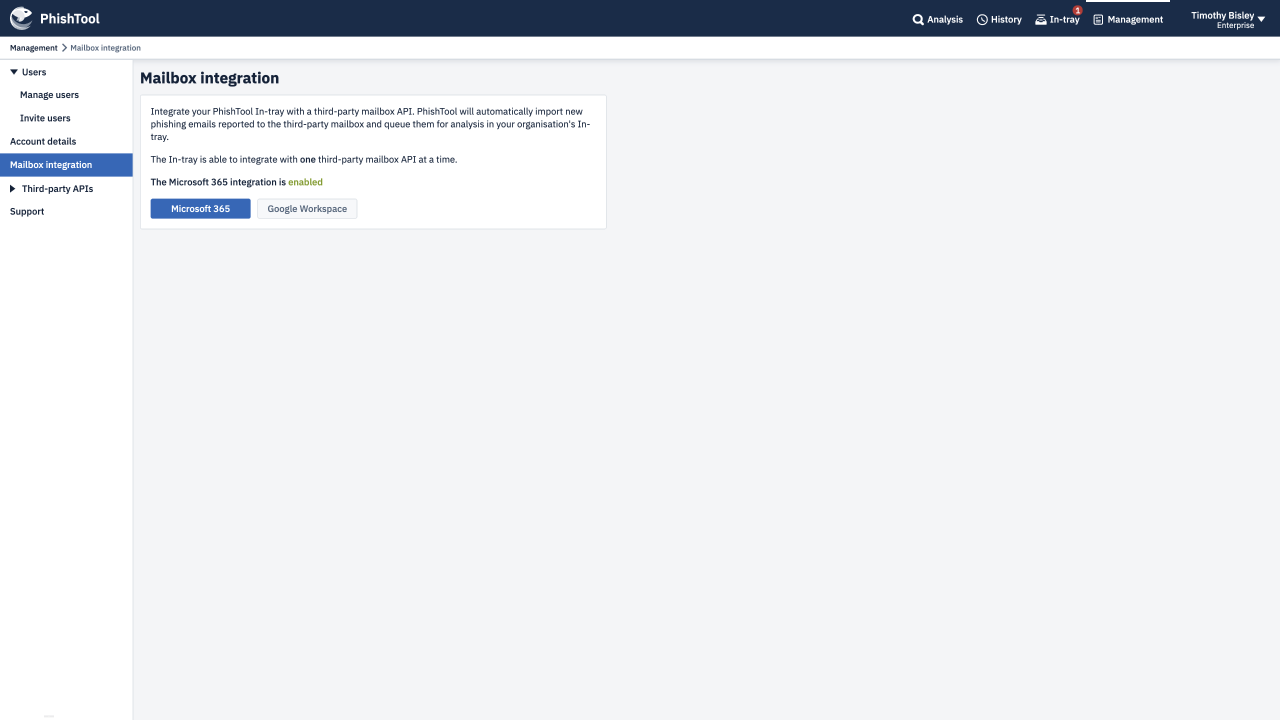
Leverage Microsoft 365 and Google Workspace integrations to instantly add the power of PhishTool to your existing phishing workflow, without configuration.
Schedule a demo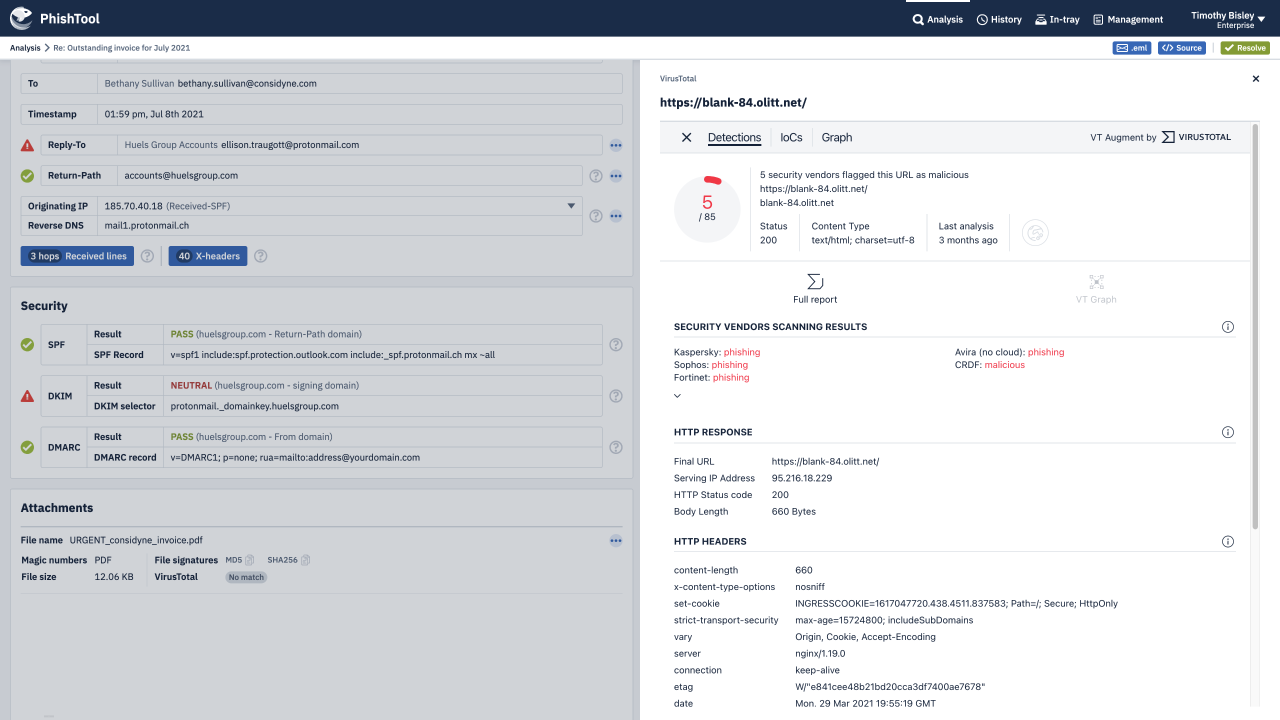
A new, intelligent approach to the phishing problem
Phishing is a persistent threat to us all, accelerated by the incredible effectiveness of phishing campaigns globally, resulting in increasingly severe financial and reputational losses.
The tired old 'appliance' based approach to email security, and the buzzword riddled solutions touting 'AI' as a silver bullet, are evidently failing. A new approach is required. PhishTool treats phishing for what it is - the number one threat to you and your organisation's security.
Find out moreProven in action
It is wise to avoid revealing the tools of your tradecraft, to remain ahead of your adversaries. For that reason we do not make public the names of those that use PhishTool to secure themselves and their organisations.
Here are just some of the sectors where organisations are protected by PhishTool.
FINANCE, LAW ENFORCEMENT, TELECOMS, INTEL, MARITIME, AEROSPACE, AUTOMOTIVE, MEDIA, ENERGY, HEALTH CARE, GOVERNMENT, AND MORE...
PhishTool
PhishTool Limited, International House,
36-38 Cornhill,
London,
EC3V 3NG,
United Kingdom
Copyright © 2025 PhishTool Limited. All rights reserved.